Introducing – AttackForge Portfolios!
You may have noticed from the title that this blog post is different from our usual posts about scheduled releases like most in the past. And there is a good reason for this. AttackForge has always focused on making the life of all people involved in pentesting easier. This time we have a new feature, or should I say – The Feature that all Enterprises need – introducing Portfolio module.
This feature is for the unsung heroes of pentesting. The people who rarely make it to the spotlight, however they keep the wheels spinning on the pentest bus. The people who are rarely praised when one yells “I’ve got shell!”. The people who transform vulnerabilities into dreaded CxO and Board Reports. This feature is for you!
There is a familiar challenge for anyone who has ever run an enterprise pentesting program across divisions, platforms, geographies, and calendar years. The challenge is to how to make sense of all those pentests (and millions of dollars spent on them) to CxOs, Risk and Compliance Committees, and ultimately people who make (and take away) security budgets – the Boards.
Boards and CxOs need to know more than just how many pentests were run across entire organisation, or even how many vulnerabilities were found across the enterprise.
They want to know how this affects the business, technology, and the risk posture of the organisation.
Below is the small subset of the questions that Boards and CxOs are asking our clients:
What is the exposure of our Internet facing applications? How many critical vulnerabilities are currently open on these platforms?
This is a very important piece of information as internet facing applications are the most exposed to adversaries. Many jurisdictions and regulators require specific pentesting processes for internet facing assets.
How can we be sure that each business division has pentested everything they need to have tested?
This is usually the next question, and it is about understanding the level of assurance the organisation has that everything that *must* be tested has actually been tested.
How are platforms fixing vulnerabilities? Is it done within the required timeframes agreed in our internal policies or set by external regulators?
Remediation of vulnerabilities means reduction of business risks. Also - doing it within prescribed timeframes means the difference between keeping the business going, receiving a fine or being shut down by a regulator, or being sued for failing contractual requirements.
How do our applications compare between 1st quarter and 2nd quarter? Are we getting any better?
Knowing how your systems are tracking over time can help the board in understanding how exposed the organisation really is, which directly translates into risk for the shareholders.
How are different business divisions and platforms comparing against each other? Where are you going to focus resources for next period?
It is important to know who is working hard and doing a good job at keeping the organisation safe, and others who may require additional resources or attention to help them improve.
Which external suppliers are lagging behind?
Enterprises need to understand their supply-chain risks, and ability to identify quickly when new risks are uncovered.
Introducing Portfolios – providing answers to the questions you just read, and many others.
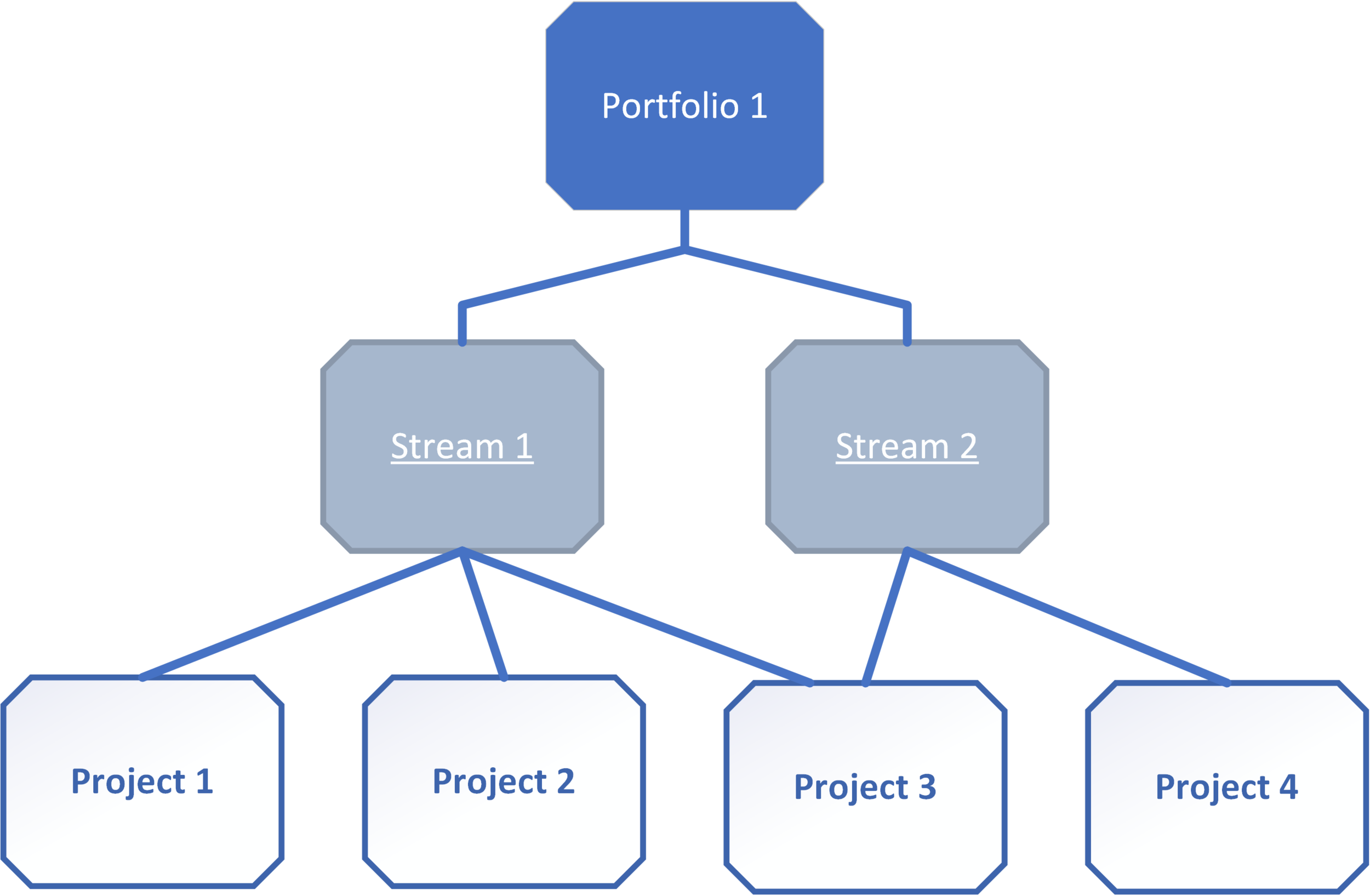
Each Portfolio represents a high-level grouping of your entire pentesting program(s). Every portfolio is made up of work streams – collection of pentests which focus on specific areas within the portfolio to tell a story.
The data to answer those questions is in AttackForge, and it means it is within our reach. Let’s see how we can answer those questions being asked by CxOs and Boards:
What is the exposure of our Internet facing applications? How many critical vulnerabilities are currently open on these platforms?
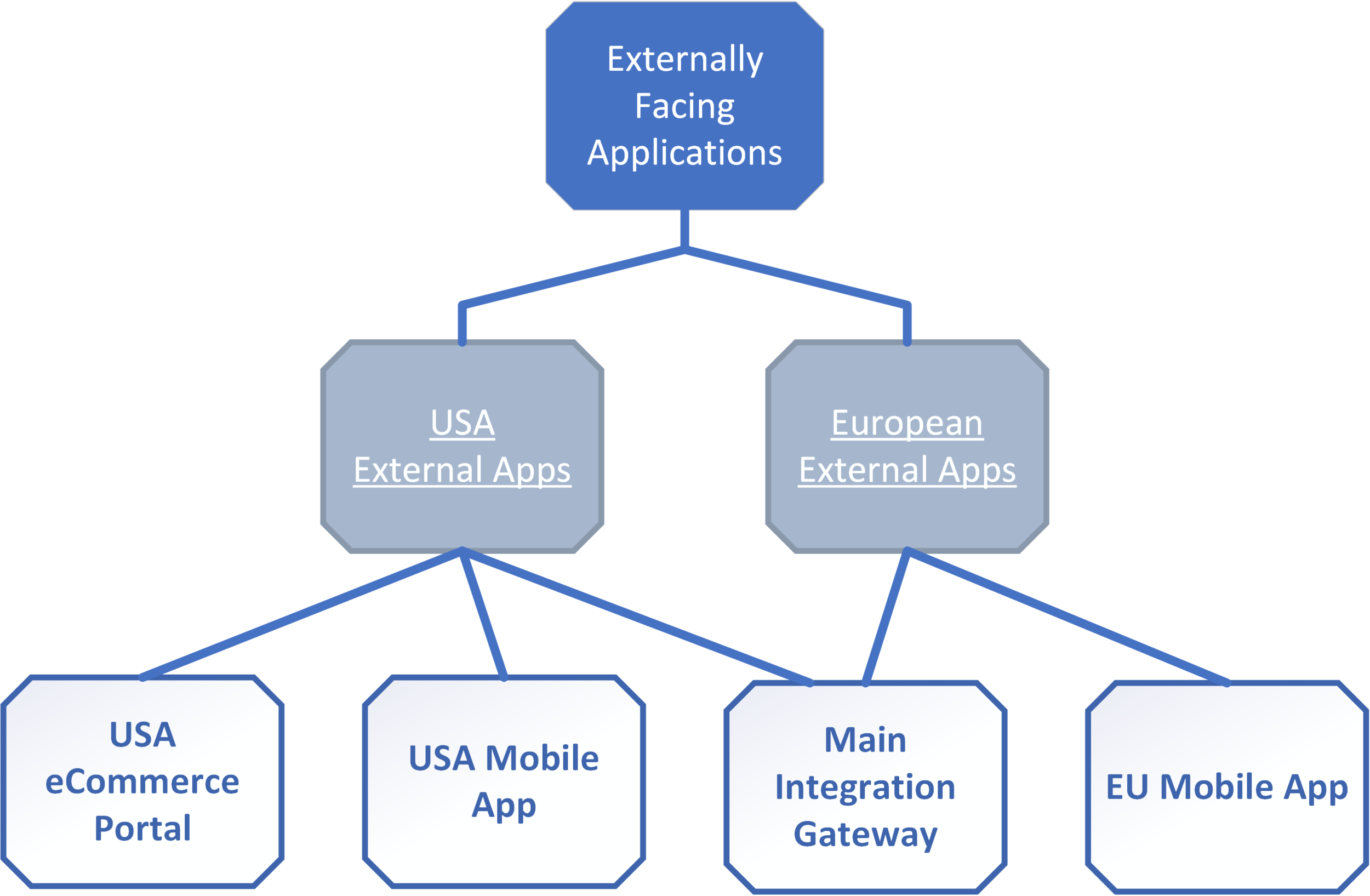
Let’s start by creating an “Externally Facing Applications” portfolio in AttackForge. Then we create work streams relevant to our organisation. In this this case it is based on the regions that these applications target.
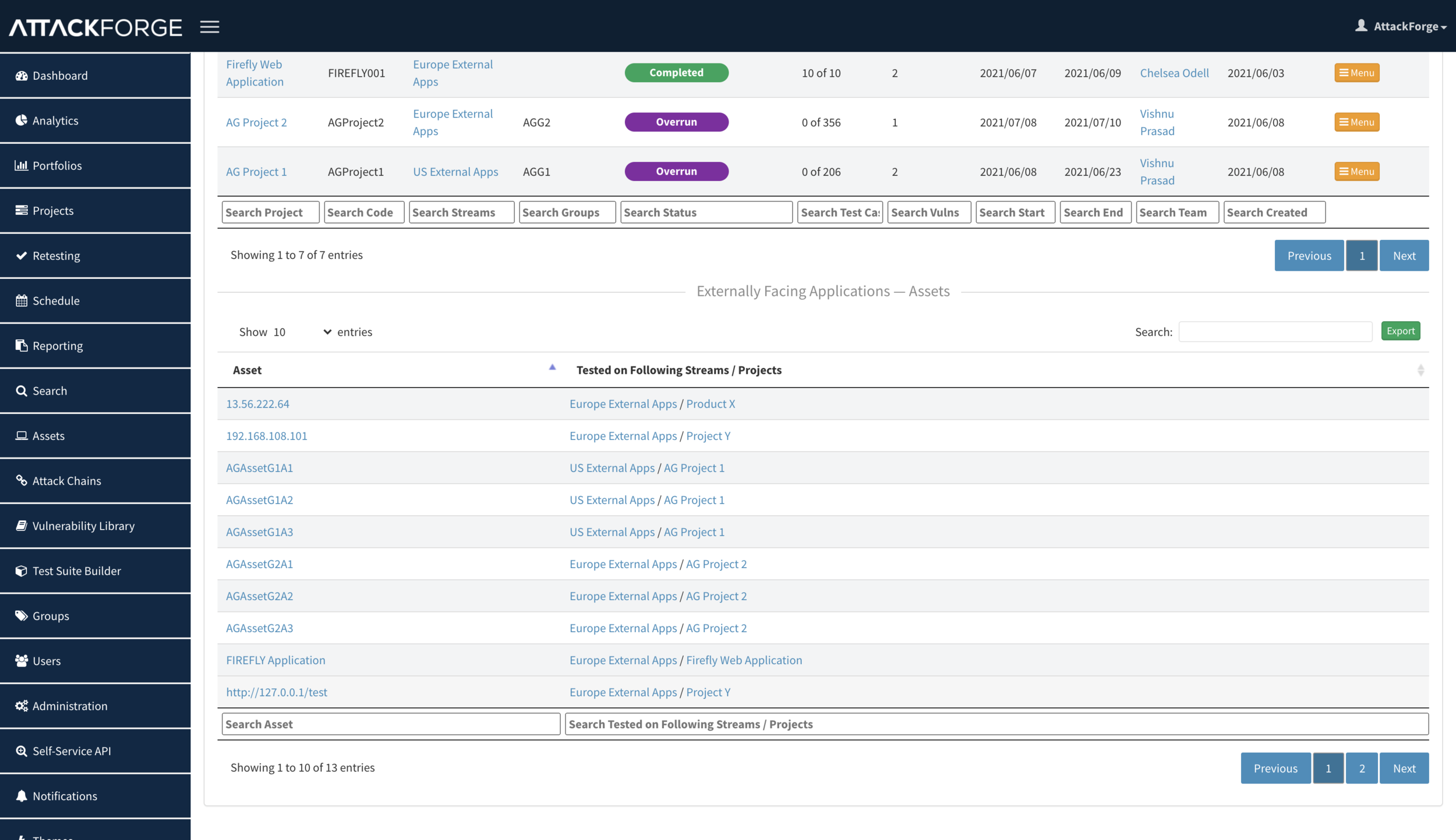
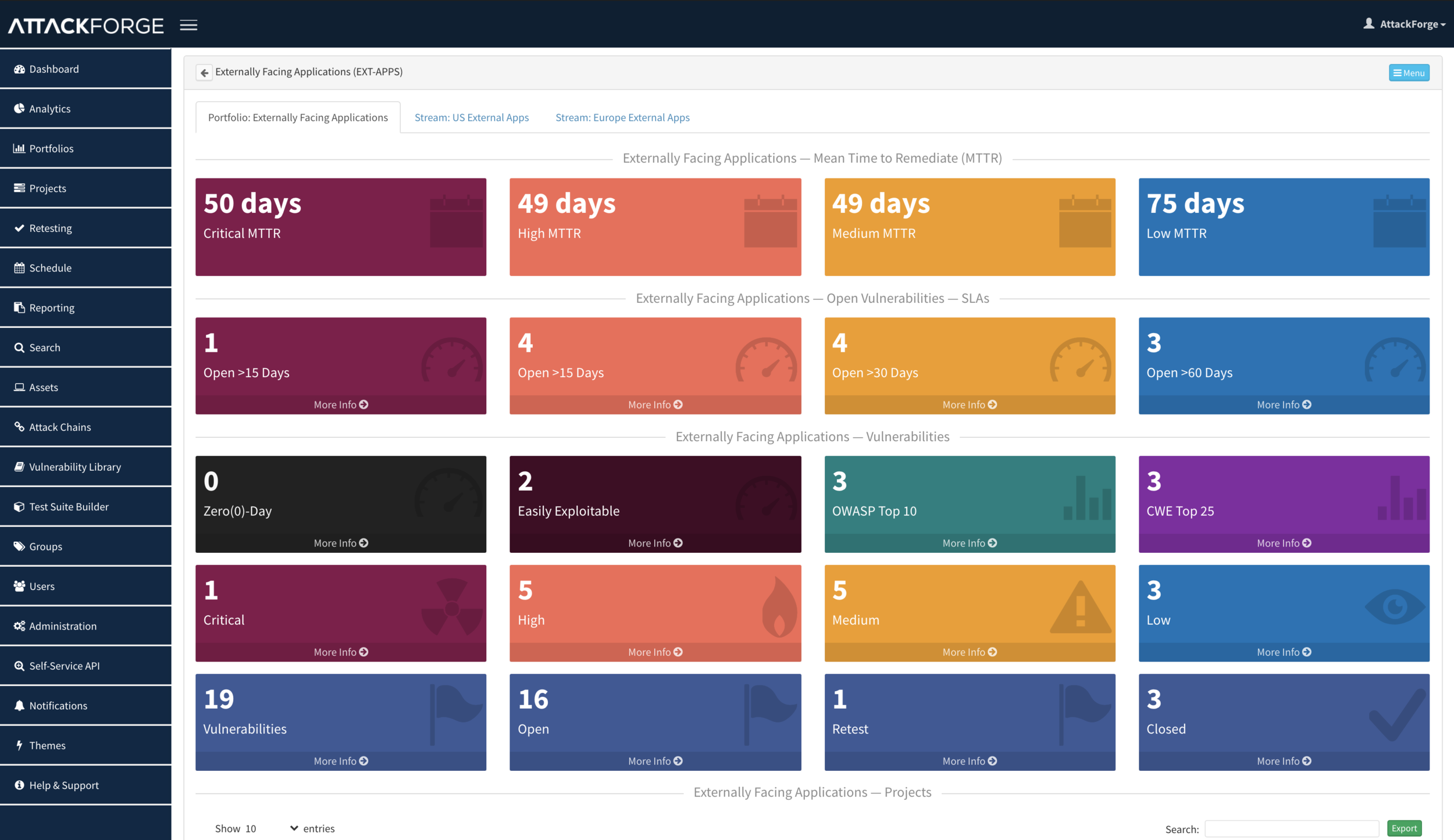
Now, when we need to produce a slide for our monthly report on the security posture of all externally facing applications, we can go to the “Externally Facing Applications” portfolio and see it all on one page, just like on the screenshot below. You can see the number of Critical and High vulnerabilities on the screen, and drill-down to underlying data if needed.
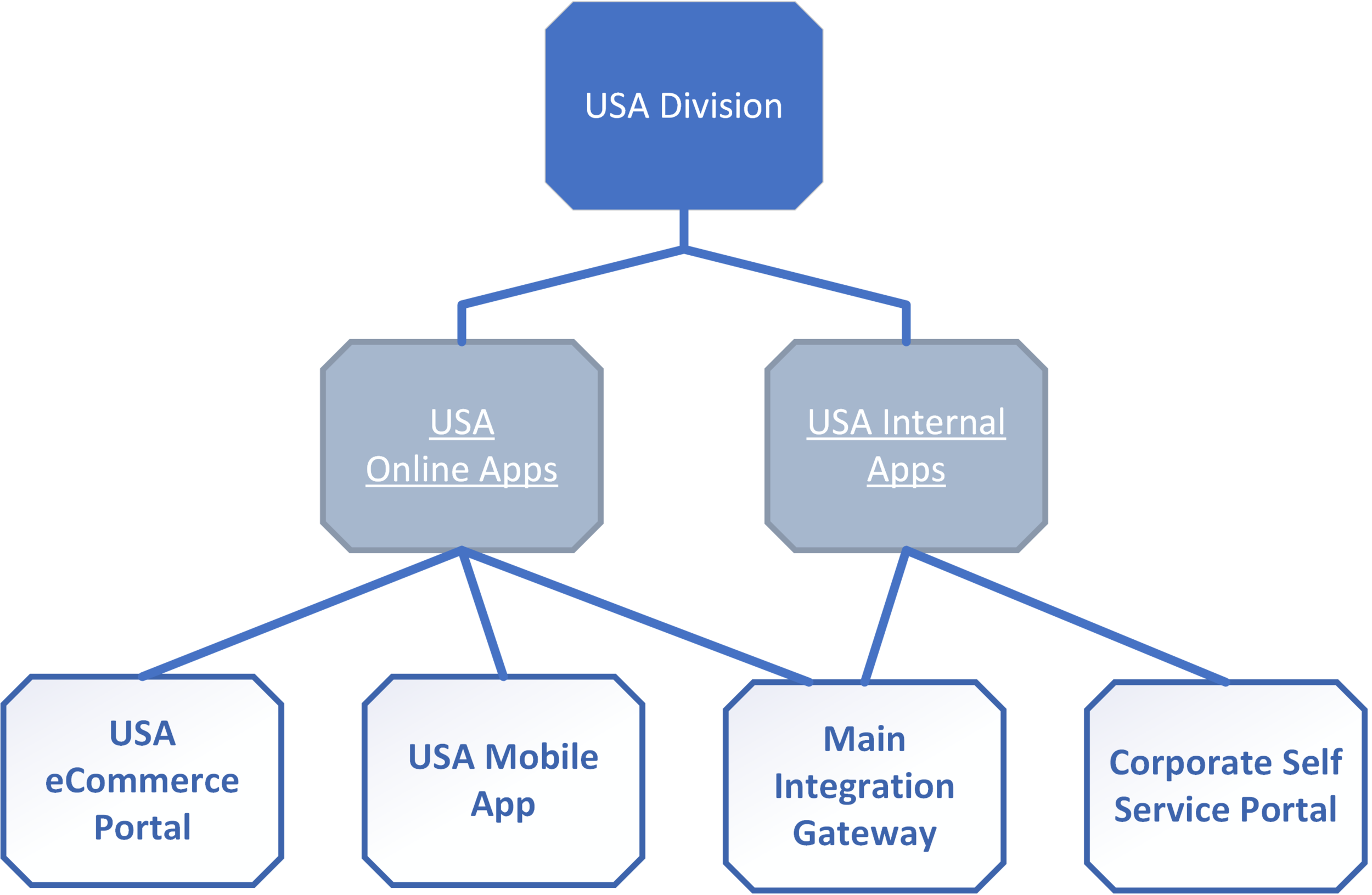
Now let’s say we need a breakdown across all applications within a division. We can create a portfolio and have necessary information again all on one screen.
Projects (pentests) could (and often should) naturally belong to multiple work streams and portfolios – making AttackForge Portfolios even more versatile. This is normal. A pentest might be tracked as part of different portfolios and work streams for different reporting purposes.
Now the only thing left is to copy the required information into your monthly report.
How can we be sure that each business division has pentested everything they need to have tested?
This is easy with portfolios – just check if all the assets that need to be tested are listed on the Asset Table for the relevant Portfolio or Work Stream page. And export it into CSV if needed.
How are platforms fixing vulnerabilities? Is it done within the required timeframes agreed in our internal policies or external regulators?
This information is available for Portfolios and Work Streams – MTTR and SLAs are listed and ready to be put in the PowerPoint. Export into CSV is also available, like for every other table in AttackForge.
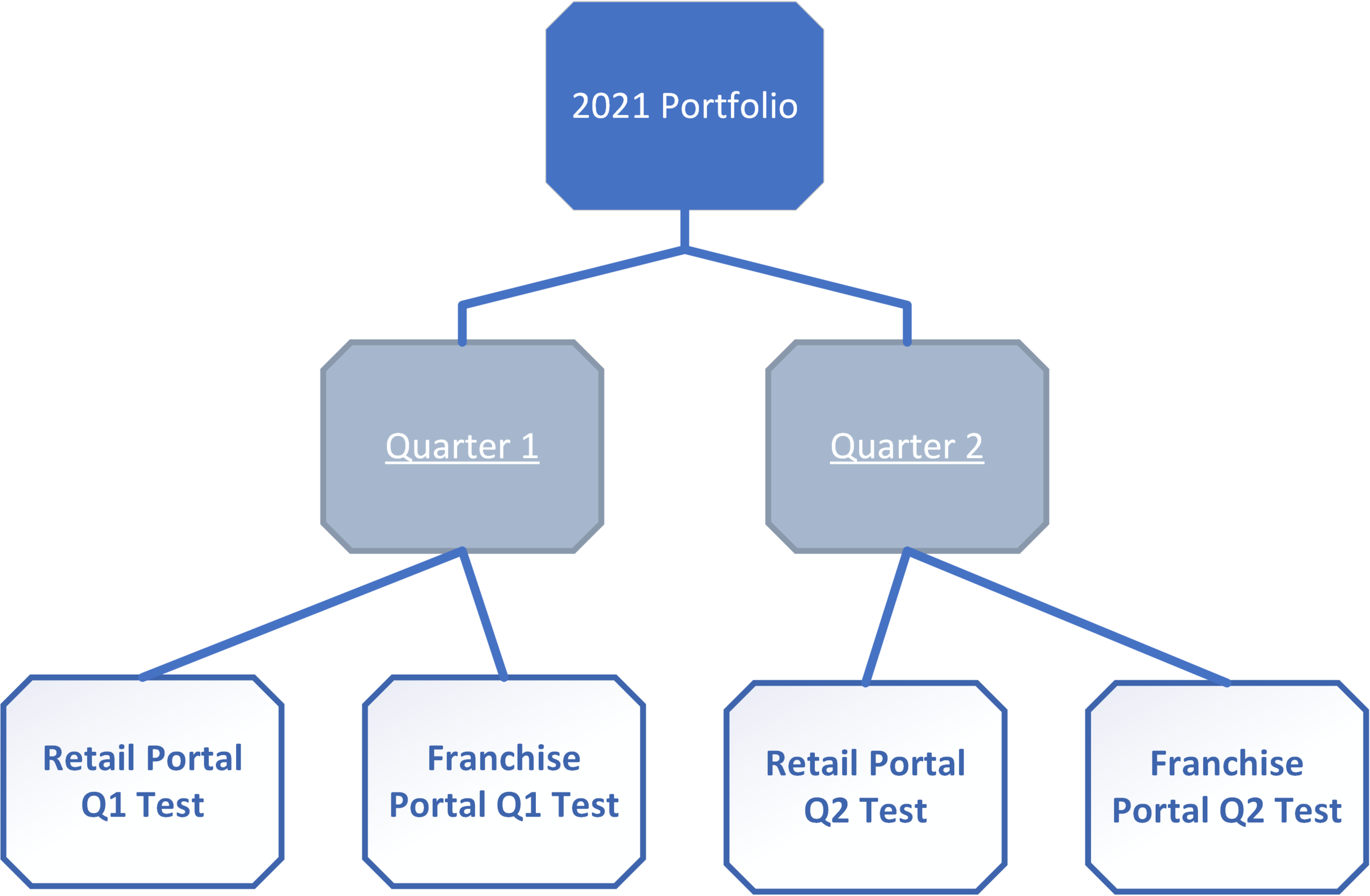
How do our applications compare between 1st quarter and 2nd quarter? Are we getting any better?
You can create a portfolio for the entire year, followed by quarterly work streams - then add the relevant projects to each quarter:
Other questions can be answered by creating the relevant portfolios (for each division, supplier, etc) and comparing them. After all – with all the information already tracked in AttackForge (and not in the PDF files) you can have all the data you need at your fingertips!
Plans for the Future
We are going to extend Portfolio functionality, allow our customers to access the data through our extensive RESTful API and our brand-new Events API (this would be the subject of the next post).
Let us know what you think. We are also interested in understanding what questions are your CxOs and Boards asking you? We can show you how those questions can hopefully get answered easily and on-demand through AttackForge modules and features.