New Release: June 2020
This month we have an action-packed release with updates to AttackChains, Service Catalogue, CVSS Scoring, New Workflows; and UI Improvements.
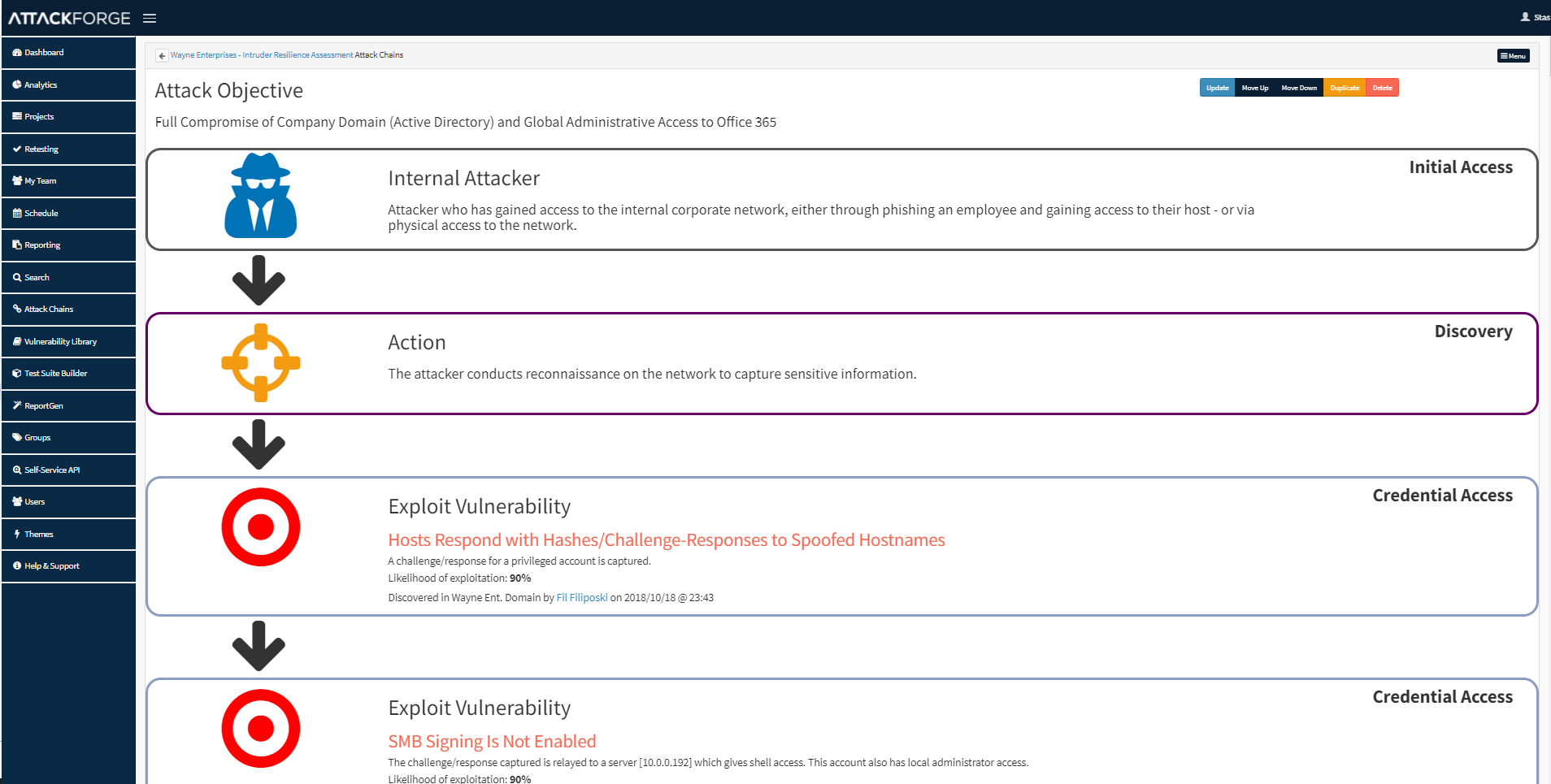
Attack Chains Now Map to MITRE ATT&CK Framework
We all have been in a room with executives, presenting serious findings from a recent pentest. You spend days meticulously planning and preparing for the discussion, only to find that you may as well be speaking a different language. The executives don’t get it. There is confusion amongst everyone. The only thing that can be agreed on is that there is no agreement on the risk rating.
A couple years back, AttackForge built a solution to this problem - Attack Chains. Attack Chains have been helping pentesters to turn technical vulnerabilities into a narrative or story about how those vulnerabilities relate to & impact on the business. Instead of arguing about risk ratings & hypotheticals, Attack Chains allow you to focus on how those vulnerabilities lead to an event - such as compromise of a server, perimeter or even company network & crown jewels – and to tell a story the business understands, so they can make informed decisions.
So now you can map your Attack Chains to MITRE ATT&CK Framework.
MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. In short – it’s what the ‘bad guys’ are doing in order to exploit your systems and compromise your assets.
Mapping AttackChains to MITRE ATT&CK Framework helps you & your business better understand how each link in the attack chain can be leveraged or exploited by a real-world threat actor. Using this mapping, you can make more informed decisions when it comes to protecting your assets & crown jewels.
For pentesters, mapping to MITRE ATT&CK Framework helps you articulate your findings better to the business, so when it’s a ‘Critical’ finding – people understand why.
You can map each link in the Attack Chain story to a specific MITRE ATT&CK Framework phase and present your Attack Chains in the context of a widely adopted framework.
Service Catalogue Now Available to Your Customers
In my time working for a big bank, the business unit I looked after was performing a vast number of pentests per year as part of their pentesting program for BAU & Project streams. Different vendors & pentesters. Different project managers. And year after year the program grew larger and larger – upwards of 400 pentests per year.
When you operate a pentesting program at scale, clarity and simplicity become a must have. Every other day a new pentest had to be scoped and negotiated between business, technology and pentesting providers. At times it was frustrating & challenging to manage communications and enforce consistency & standardization.
Since inception, AttackForge had pre-built methodologies (Test Suites) to ensure consistency in pentesting, and uniform approach to security testing assessments and pentesting.
In this release, we have transformed project request workflow to utilise a Service Catalogue model. AttackForge allows you to set up a catalogue of security testing services that your customer can request through AttackForge. Transparency is built into the process from end-to-end. There is visibility of exactly how many test cases will be performed by the assessor/pentester. This reduces time & effort for both the customer & security team when scoping & planning for a pentest.
Daily Tracker Now Includes Color-Coding
As a manager you need to check progress daily on your pentests. We have now color coded the daily tracker to make it much easier to identify key important data on how your project is tracking, and make it easier on your eyes.
That’s all for today. See you next time.